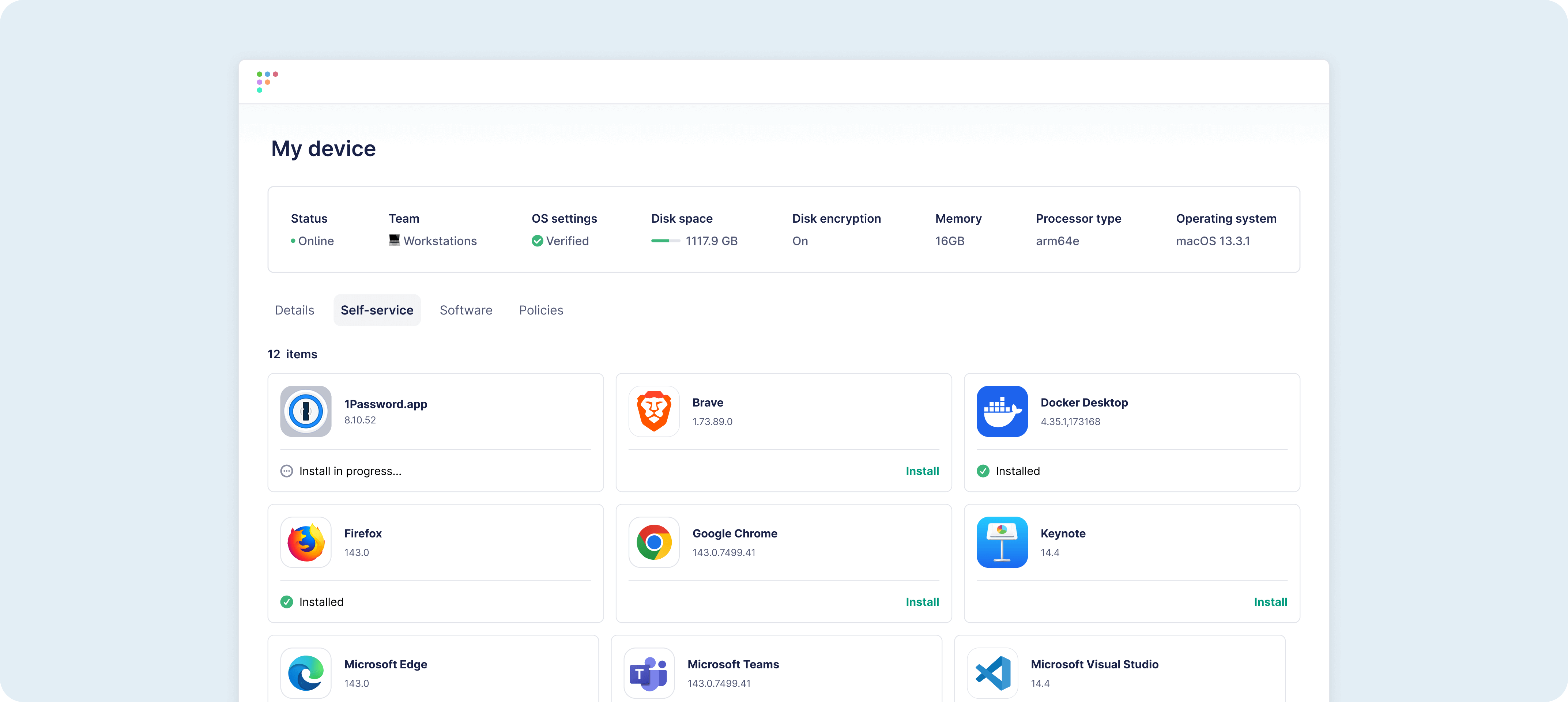
Software management
Manage software consistently
Pick from a curated software catalog or upload your own custom packages. Configure custom installation scripts if you need or let Fleet do it for you.
This is not just production osquery, but actually a way bigger opportunity than even something like Airwatch or Jamf.

Eric Tan
CIO & Chief Security Officer at Flock Safety

Deploy software your own way
Deploy software from any source using the method that works best for you—whether it's through the UI, API, or GitOps.
Install from a built-in catalog of Fleet-maintained apps without the need for additional configuration.
Upload any third-party software as a custom package to deploy all of the tools your end users need.
Manage app deployments and updates for your computers and mobile devices from app stores.
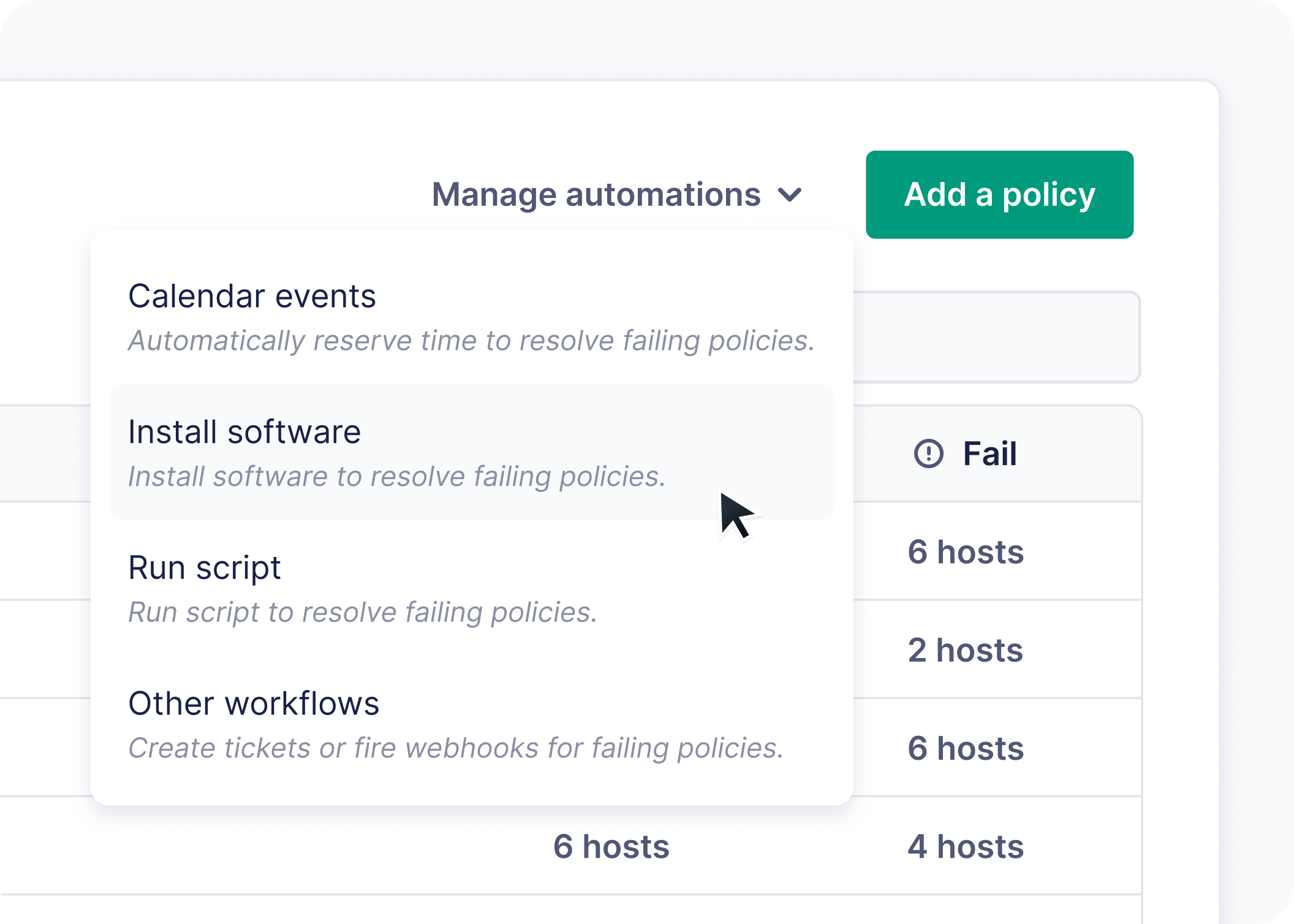
Automate patch management
Take the guesswork out of keeping devices up-to-date and secure by asking yes or no questions tied to automations.
Use policy automations to trigger app updates, execute scripts, or create tickets in Jira and Zendesk.
Generate webhooks to integrate with your favorite tools and systems.
Optionally integrate Google Calendar to schedule time for your users to update software when it’s convenient for them.

The right software at the right moment
Use self-service to keep employees productive and secure with software curated to their needs.
Install organization-approved software for macOS, Windows, and Linux.
Quickly deliver software for teams of any size, tailored to small groups or the entire organization.
Fleet lets us be more actionable with fewer people. It helps us to filter out the noise better than we could with the other big name products we replaced.

Andre Shields
Cybersecurity Security Engineer, Vulnerability Management

Mitigate CVEs automatically
Build automations that close tickets or mitigate vulnerabilities by updating or removing software and running custom scripts.
Automatically detect when old vulnerabilities are reintroduced, or mitigations falter.
Track and mitigate zero days, with live queries and policies, even before they're officially published as CVEs.
Only create tickets for vulnerabilities that affect your environment. Automate ticketing with Jira, ServiceNow, or integrate your own system.
Deep-link live data with internal IT and platform teams.
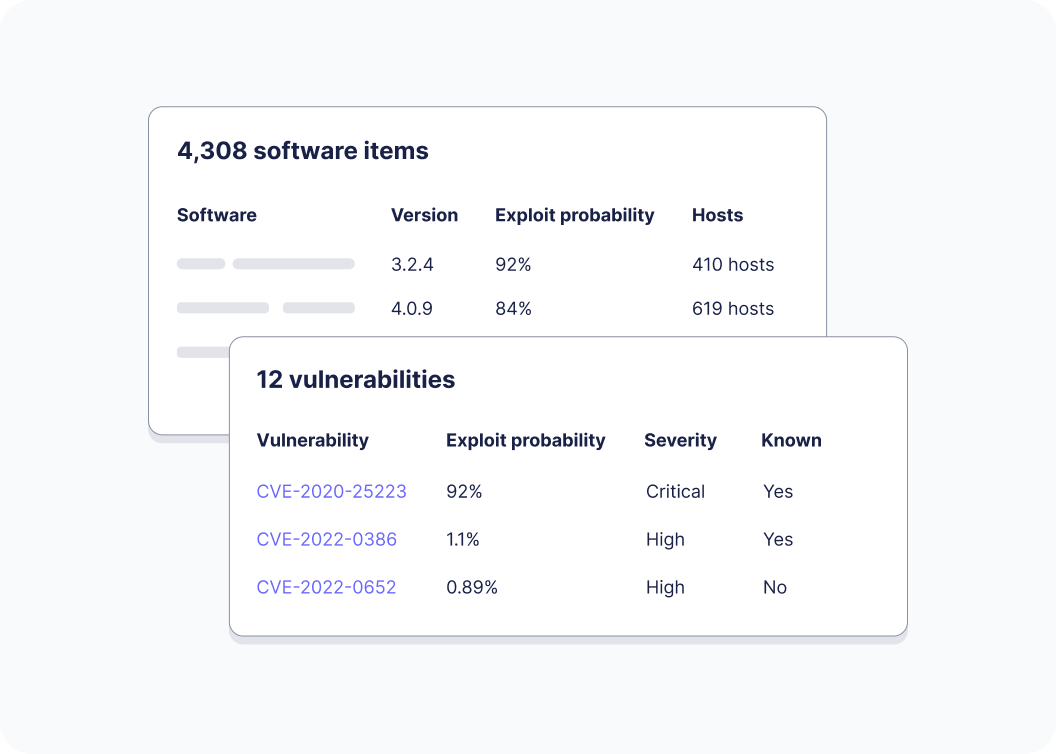
Deep context from the environment
Fleet gives you data down to the chip level on every endpoint to help you make sense of which vulnerabilities to prioritize.
Automate prioritization with an admin-level agent that has visibility down to the chipset of any endpoint
Access over 300 tables of system state data. Use presets or create your own queries.
Automatically match CVEs to your operating systems, apps, extensions, browser plugins, Python libraries, everything.
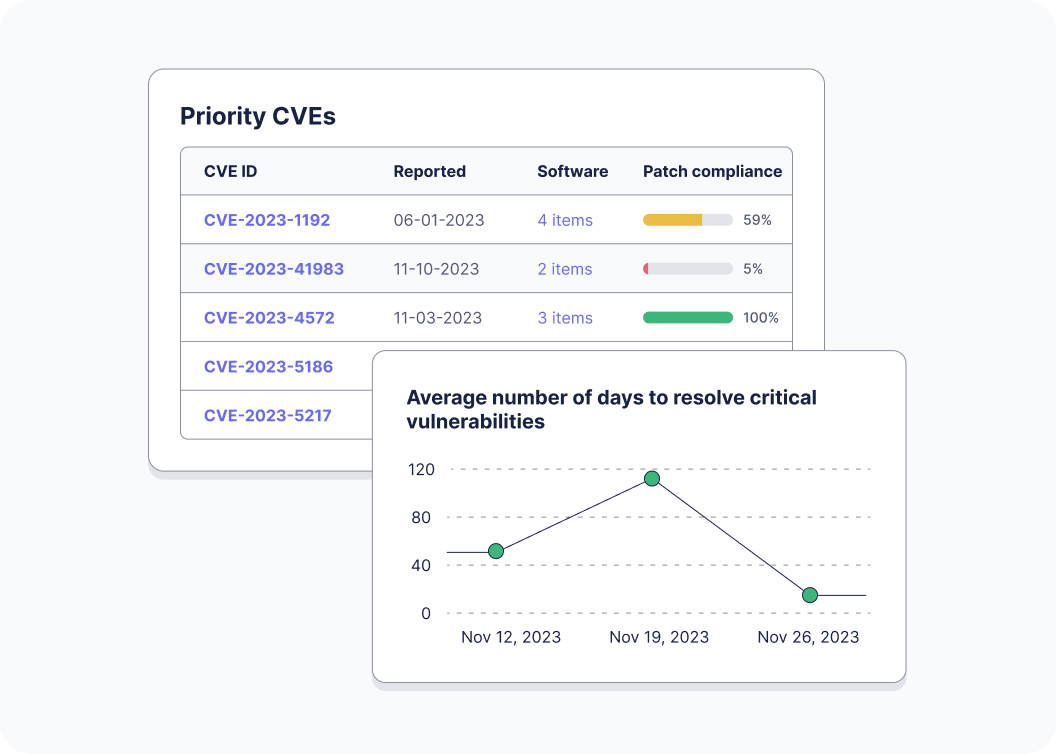
Report what matters
Let's face it, most built-in graphs leave you wanting more. Report MTTR and any other custom metrics exactly the way you want to using fresh data from real computers.
Track any “celebrity” CVE across every OS, every cloud, and every device, and show how quickly it was mitigated.
Avoid distracting your CISO with bloated reports. Only communicate facts important to your organization's KPIs. Show real-time mitigation progress (%) or sync with your favorite data tool like Microsoft BI.
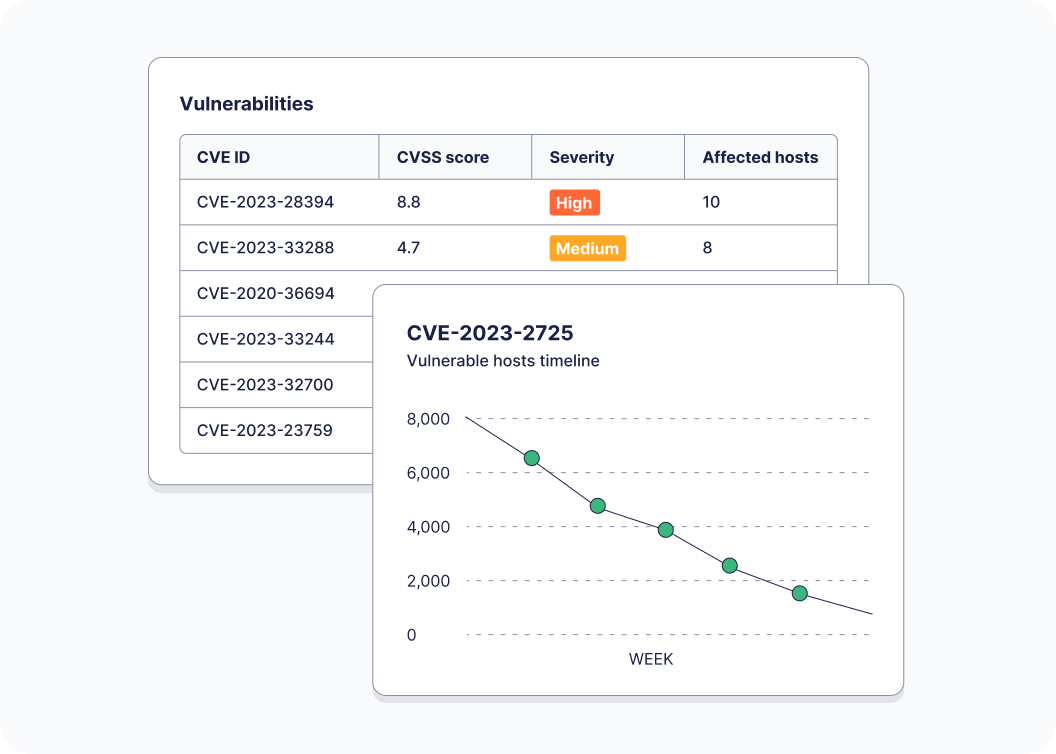
Up-to-date data without scans
Traditional network vulnerability scans can clog your network and even haunt your printers with pages full of wingdings. Fleet does things differently.
Eliminate the risk of side effects from scanning the network.
Lightweight enough for the most brittle environments (OT, data centers, embedded/BTS, low-latency gaming servers).
Quickly pull data about important CVEs and zero days during an incident or audit.
Untangle your security stack
Use open data and APIs to connect your vulnerability solution with osquery, the agent you might already have deployed.
Normalize asset management data and software inventories from multiple tools and operating systems.
Help teams work on vulnerabilities that have actually been exploited (CISA KEVs) or have a high probability of being exploited (EPSS), or whatever is important in your environment.
Process CVEs across cloud and non-cloud assets in a single platform and see who's responsible for what.