
Secureframe Agent
Build trust with customers using automation backed by world-class experts
Why is Fleet on my computer?
Secureframe Agent is built on Fleet. Fleet makes it a little easier for your IT team to keep your computer healthy without interfering with your work.
How does it affect me?
Secureframe Agent has to monitor compliance with a bunch of security requirements. But we also realize you have a job to do. So we want to be as un-intrusive as possible.
Your IT team has to maintain your computer and keep it compliant with a bunch of security requirements. But they also realize you have a job to do. So they want to be as un-intrusive as possible.
That’s why they chose Fleet. It’s compatible with everything, including Linux, so it doesn’t limit what operating system you use. And it’s open source, meaning if you want to, you can take it apart and see what it’s doing to your computer.
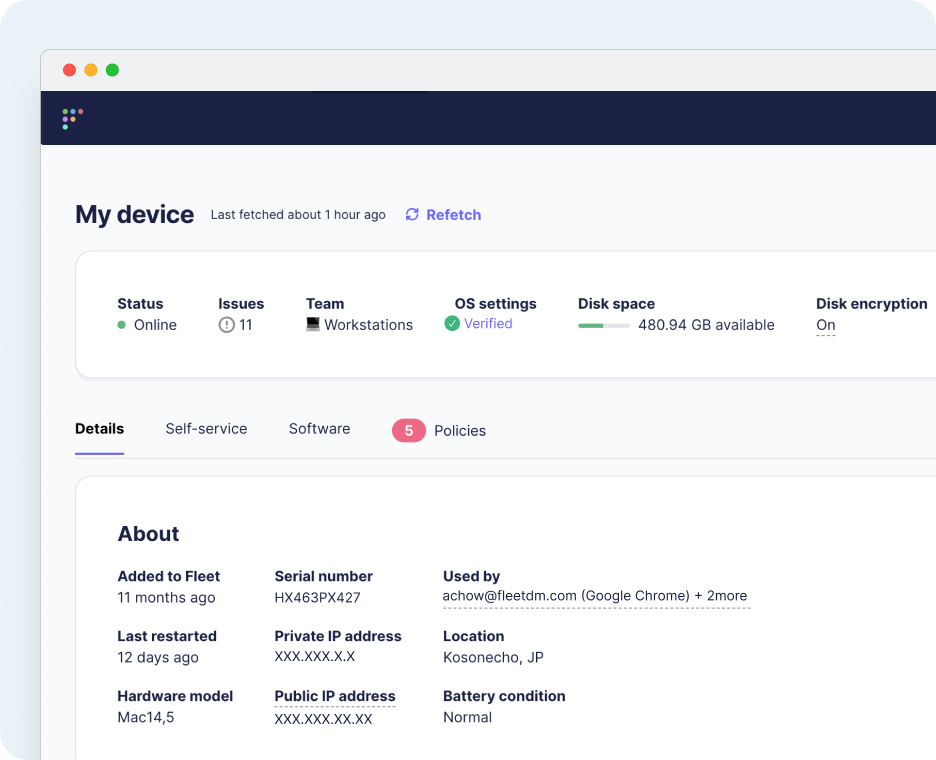
What personal information can Secureframe see?
Here’s what Fleet can see on your computer:
On/off status
Fleet knows when your device is on or off. This is shown via the online/offline status in Fleet Desktop. This is useful for understanding the state of your device and for troubleshooting should a problem ever arise.
System settings
Fleet can read settings like minimum password length on your device.
Software
Fleet can access a detailed list of the apps and other software installed on your device.
Security configurations
Fleet can see information about the status of firewalls and other security software installed on your device.
Fleet can't guarantee that other personal data isn't being captured by user activity monitoring or cybersecurity tools like Veriato, CrowdStrike, etc.
FAQ
Can the Fleet icon be disabled for the Agent?
No, the Fleet Agent icon cannot be disabled at this time.
Did any permissions change with this update?
No, This update does not change Secureframe Agent’s functionality or its read-only access permissions.
What does a device check-in involve and what do I need to do?
- This particular device check-in is a one time action.
- Once the update is installed, users will notice a new icon in the status bar and your maintenance is complete.
- Devices simply need to be online for approximately 5 minutes to receive the update.
What if the device check-in doesn't work for some users?
Secureframe will provide a full list of devices that did not properly check-in so Admins are able to resolve individually, if needed
What personal information can Fleet see?
Here’s what Fleet can manage on your computer:
On/off status
Fleet knows when your device is on or off. This is shown via the online/offline status in Fleet Desktop. This is useful for understanding the state of your device and for troubleshooting should a problem ever arise.
Browser history
Fleet can see browser history to protect you in the rare event of bad actors gaining access to you device and personal information.
System settings
Fleet can enforce settings like password length on your device. This is useful for IT teams to keep your Mac up to date so you don’t have to.
Wi-Fi settings
To help connect you to your corporate Wi-Fi or VPN, Fleet can configure Wi-Fi settings and install certificates on your device.
Remote actions
Device actions are helpful for IT teams to troubleshoot your device remotely if you run into any issues. If your IT team uses Fleet's device management (MDM) features, your computer can be restarted, locked or even wiped remotely by your administrator.
Shell scripts
Fleet can run any shell script on your device remotely. This is useful for IT teams to help you troubleshoot remotely if you run into any issues with your device.
User account logins
Fleet can see details about the user accounts associated with your device, including which accounts have logged in recently. This is useful for IT and security teams to identify logins from suspicious accounts.
Fleet can also block logins from devices that don't meet your organization's policies. This allows IT teams to keep your accounts secure.
Device health & performance
Fleet can see details about your device’s hardware. E.g., what processor is used, how much memory is installed, storage capacity, battery health, etc. This allows IT teams to preemptively address device health problems, which can mitigate data loss and reduce disruption to your workflow caused by IT related issues.
Software
Fleet can add apps, remove apps, update software, and access a detailed list of the apps and other software installed on your device. This enables IT teams to better manage software update schedules, and reduce disruption to your workflow. Additionally, security teams can use this data to check if any software has been compromised by referencing the version numbers against known vulnerable software databases.
Running processes
Fleet can access a list of processes running on your device. These are processes you interact with graphically i.e., opened software; and processes that are running tasks in the background, such as sending data over network connections, running backups, or scheduled auto-updates. IT and security teams can use osquery to view this list in order to detect suspicious activity that may be a threat to your system.
Security configurations
Fleet can see information about the status of firewalls and other security software installed on your device.
Connected hardware devices
Fleet can see information about connected hardware devices. This is typically limited to only the type of hardware connected, and not specific details about the device. E.g., connected smartphones, USB devices, network devices, audio/visual hardware.
Device location
Fleet uses IP geolocation to provide an approximate location of your device. Accuracy of IP geolocation services vary depending on where you are, but can typically be pinpointed within the nearest state or city. Organizations typically use this feature to track stolen or misplaced devices, and in some cases to ensure the safety of employees.
File contents
In the case of a cyber attack, it is possible with Fleet to gain read access to files on your system. This is not a feature designed for privacy invasion, but rather a means for security teams to locate files on your device that may have been created or affected by a malicious virus.
Additionally, Fleet can be configured to store disk encryption keys that can be used to recover encrypted data from a macOS device.
Fleet can't guarantee that other personal data isn't being captured by user activity monitoring or cybersecurity tools like Veriato, CrowdStrike, etc.
What can Fleet see?
Here’s what Fleet can manage on your {{guessedPlatformName}}:
On/off status
Fleet knows when your device is on or off. This is useful for understanding the state of your device and for troubleshooting should a problem ever arise.
System settings
Fleet can enforce settings like password length on your device. This is useful for IT teams to keep your device up to date so you don’t have to.
Wi-Fi settings
To help connect you to your corporate Wi-Fi or VPN, Fleet can configure Wi-Fi settings and install certificates on your device.
Remote actions
Device actions are helpful for IT teams to troubleshoot your device remotely if you run into any issues. Your device can be restarted, locked or even wiped remotely by your administrator.
Device health & performance
Fleet can see details about your device’s hardware. E.g., what processor is used, how much memory is installed, storage capacity, battery health, etc. This allows IT teams to preemptively address device health problems, which can mitigate data loss and reduce disruption to your workflow caused by IT related issues.
Software
Fleet can add apps and update software. This enables IT teams to better manage software update schedules, and reduce disruption to your workflow.







