Fleet 4.16.0 | more customization, beefed up vuln management, Jira added to integrations.
{{articleSubtitle}}
Kathy Satterlee
Fleet 4.16.0 | more customization, beefed up vuln management, Jira added to integrations.
{{articleSubtitle}}
Kathy Satterlee
Fleet 4.16.0 | more customization, beefed up vuln management, Jira added to integrations.
Fleet 4.16.0 is up and running. Check out the full changelog or continue reading to get the highlights.
For update instructions, see our upgrade guide in the Fleet docs.
Highlights
- Customize your organization's "Transparency" landing page.
- Prioritize your vulnerability management efforts.
- Automatically create Jira issues or Zendesk tickets for failing policies.
- More accurate vulnerability detection for Ubuntu hosts.
Customize your organization's "Transparency" landing page
Available in Fleet Premium
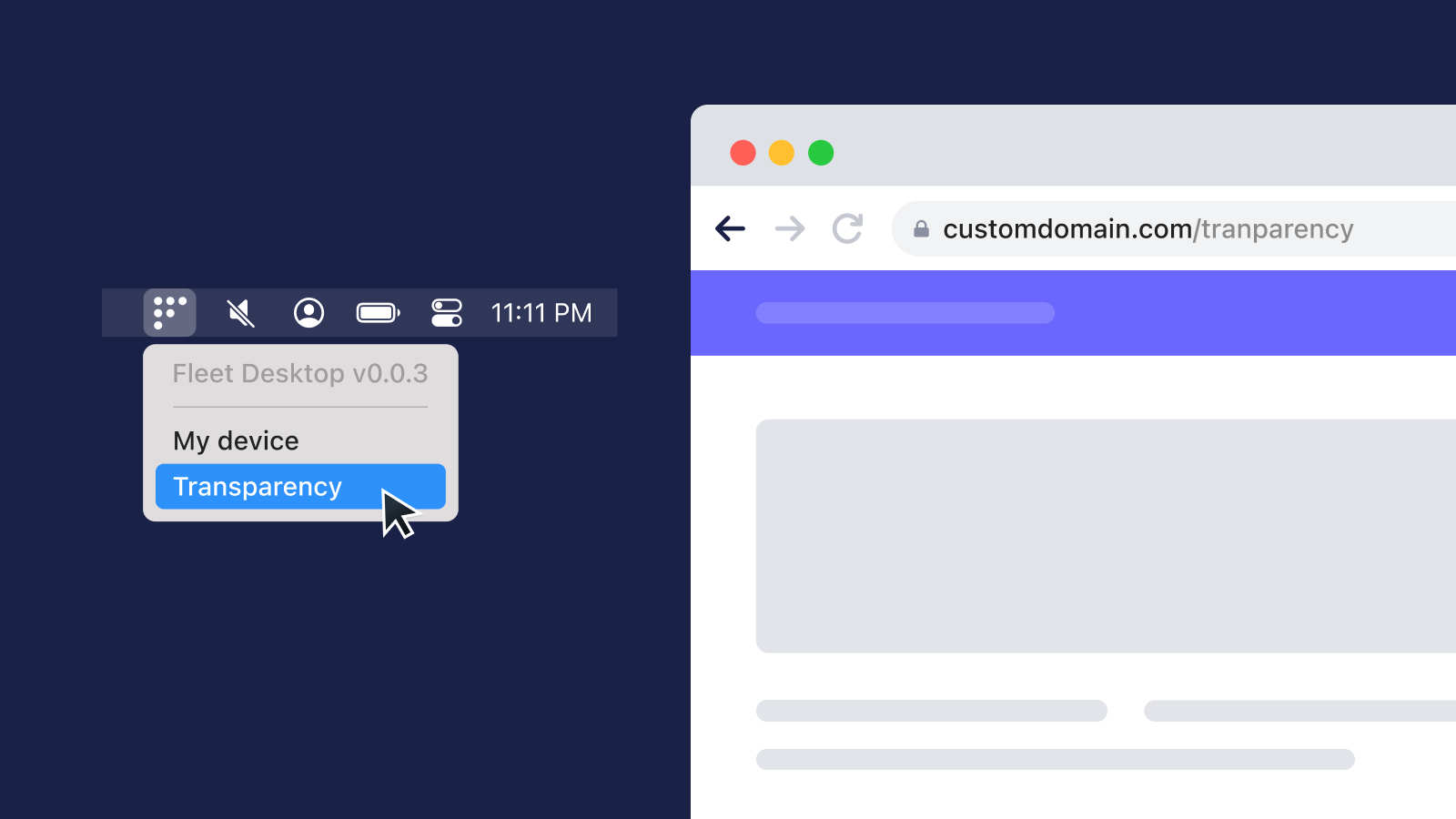 Fleet Desktop gives end-users a Transparency landing page to see what information Fleet is able to access.
Fleet Desktop gives end-users a Transparency landing page to see what information Fleet is able to access.
Fleet 4.16.0 adds settings for a custom Transparency URL. This allows you to use custom branding, as well as giving you control over what information you want to share with your end-users.
Prioritize your vulnerability management efforts
Available in Fleet Premium
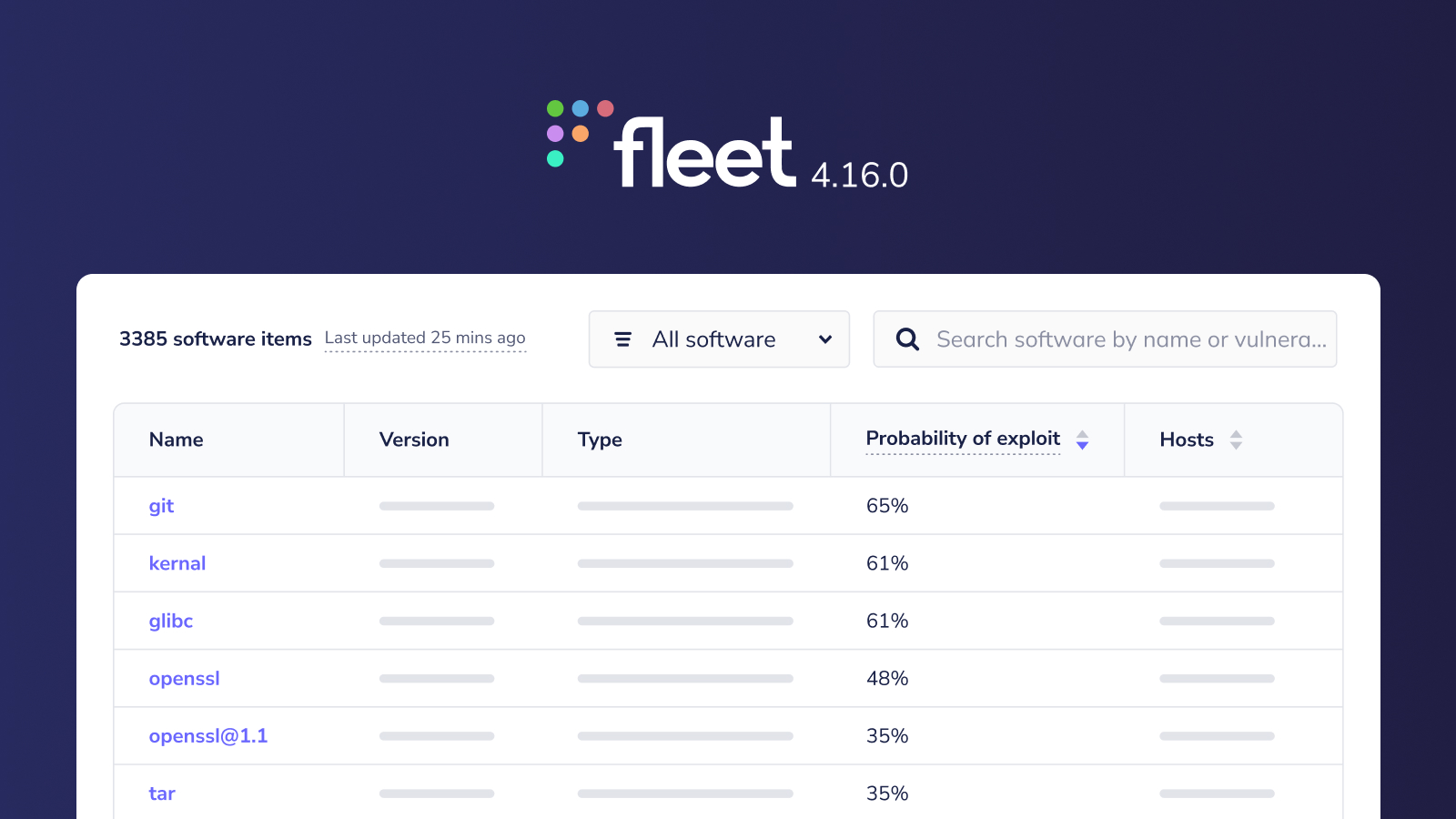
 We've added EPSS probability scores, CVSS base scores, and CISA's known exploits to Fleet's vulnerability detection. This allows you to quickly categorize which threats need attention today, next week, next month, or "someday."
We've added EPSS probability scores, CVSS base scores, and CISA's known exploits to Fleet's vulnerability detection. This allows you to quickly categorize which threats need attention today, next week, next month, or "someday."
Automatically create Jira issues or Zendesk tickets for failing policies.
Available in Fleet Free & Fleet Premium
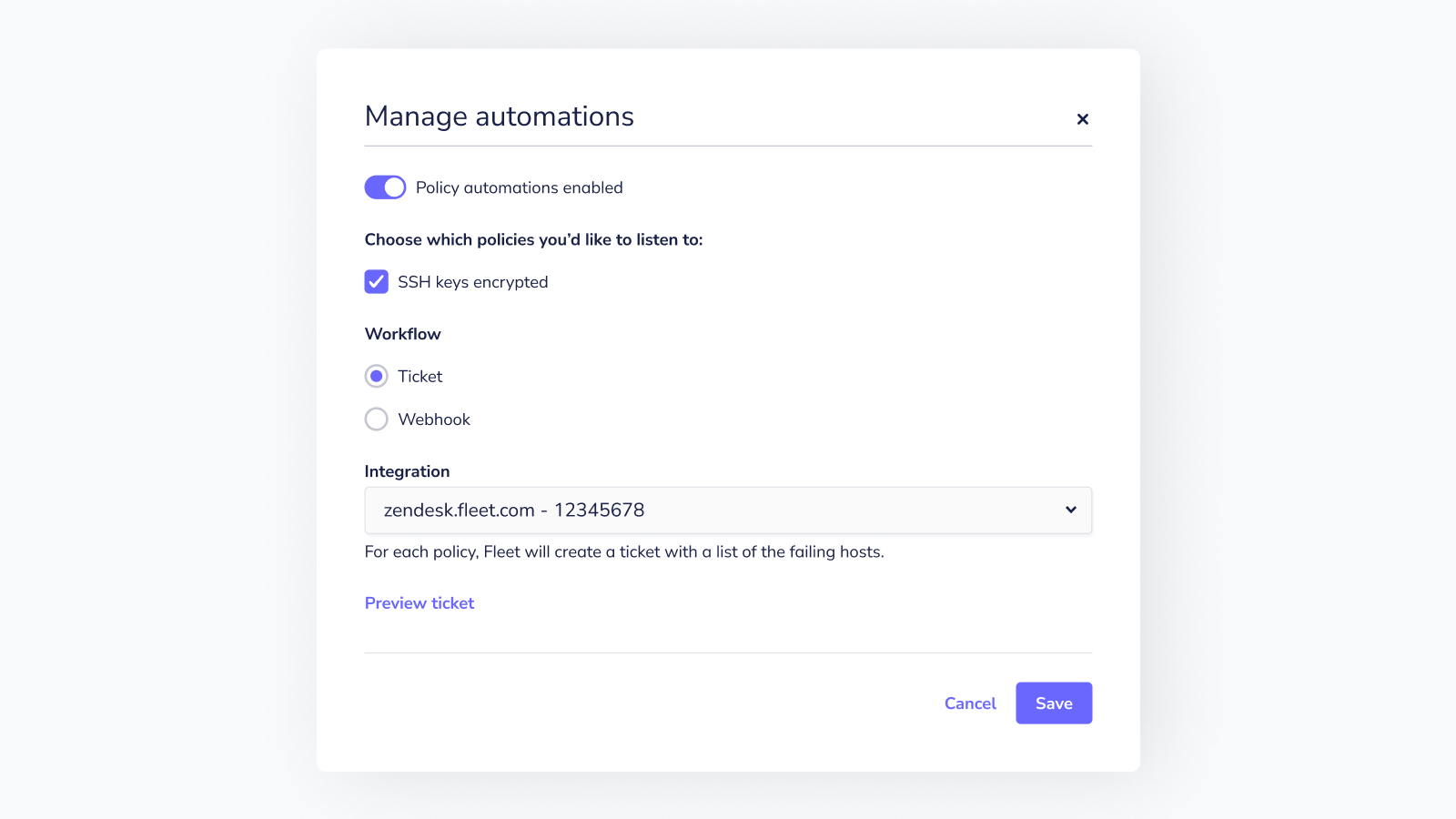 We've expanded our integration efforts to include Policies. You can configure Fleet to automatically create a Jira issue or Zendesk ticket when one or more hosts fails a specific policy. To add policies to your integrations in the Fleet UI, go to Policies >> Manage Automations and select the policies you'd like to monitor and the integration to use.
We've expanded our integration efforts to include Policies. You can configure Fleet to automatically create a Jira issue or Zendesk ticket when one or more hosts fails a specific policy. To add policies to your integrations in the Fleet UI, go to Policies >> Manage Automations and select the policies you'd like to monitor and the integration to use.
Zendesk integration is currently in beta.
More accurate vulnerability detection for Ubuntu hosts.
Available in Fleet Free & Fleet Premium
Fleet now utilizes Open Vulnerability and Assement Language (OVAL) processing for Ubuntu hosts. Adding additional data sources increases the accuracy of detected vulnerabilities.
There are ongoing efforts to include OVAL datasources in CentOS and other Linux distributions as well.
More new features, improvements, and bug fixes
In 4.16.0, we also:
Added software details page to the Fleet UI.
Improved live query experience by saving the state of selected targets and adding count of visible results when filtering columns.
Fixed an issue where the Device user page redirected to login if an expired session token was present.
Fixed an issue that caused a delay in availability of My device in Fleet Desktop.
Added support for custom headers for requests made to
fleetinstances by thefleetctlcommand.Updated to an improved
usersquery in every query we send to osquery.Fixed
no such tableerrors formdmandmunki_infofor vanilla osquery MacOS hosts.Fixed data inconsistencies in policy counts caused when a host was re-enrolled without a team or in a different one.
Fixed a bug affecting
fleetctl debugarchiveanderrorscommands on Windows.Added
/api/_version_/fleet/device/{token}/policiesto retrieve policies for a specific device. This endpoint can only be accessed with a premium license.Added
POST /targets/searchandPOST /targets/countAPI endpoints.Updated
GET /software,GET /software/{:id}, andGET /software/countendpoints to no include software that has been removed from hosts, but not cleaned up yet (orphaned).
Ready to update?
Visit our Update guide in the Fleet docs for instructions on updating to Fleet 4.16.0.







