Open orchestration
Deeper, faster visibility for every OS

Build the agent in "read-only" mode or enable remote scripting to automatically mitigate misconfigurations and vulnerabilities.
On-demand dataUse a live connection to every endpoint to simplify audit, compliance, and reporting from workstations to data centers.
Data portabilityShip data to any platform like Splunk, Snowflake, or any streaming infrastructure like AWS Kinesis and Apache Kafka.

“Osquery is one of the best tools out there and Fleet makes it even better. Highly recommend it if you want to monitor, detect and investigate threats on a scale and also for infra/sys admin. I have used it on 15k servers and it’s really scalable.”

Ahmed Elshaer
DFIR, Blue Teaming, SecOps
On-demand data
Use a live connection to every endpoint to simplify audit, compliance, and reporting from workstations to data centers.
Live connection
Talk to online devices in real time with Fleet’s live query API. Implement custom workflows like conditional access based on device posture, Identity, and more.
Software and asset inventory
Get visibility into all endpoints across any operating system*, including support for servers and containers in every cloud infrastructure.
See logins for every endpoint
Identify who logs in to any system, including login history and current sessions. Look up any computer by the email address of the person using it.
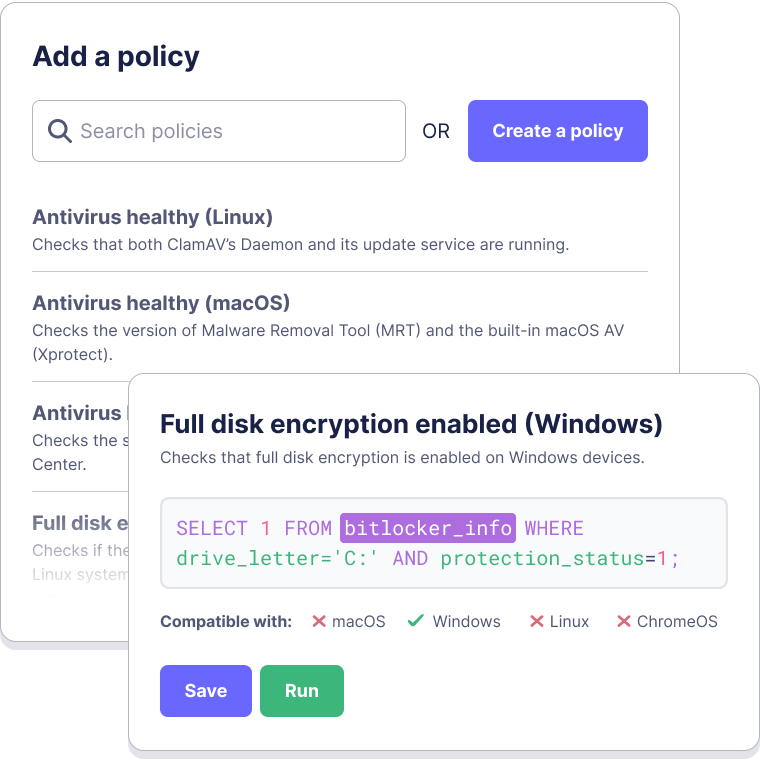
CIS benchmarks
Keep all your endpoints* compliant with customizable baselines, or use common benchmarks like CIS.
EDR health checks
Verify that your EDR tools are installed and working so you can identify and address configuration issues quickly.
Verify updates and settings
Track progress towards deadlines for security posture remediation projects, and enforce due dates through automations.
*Currently limited to: Apple, Linux, Windows, Chromebooks, OT, data centers, Amazon Web Services (AWS), Google Cloud (GCP), and the Microsoft Cloud (Azure).
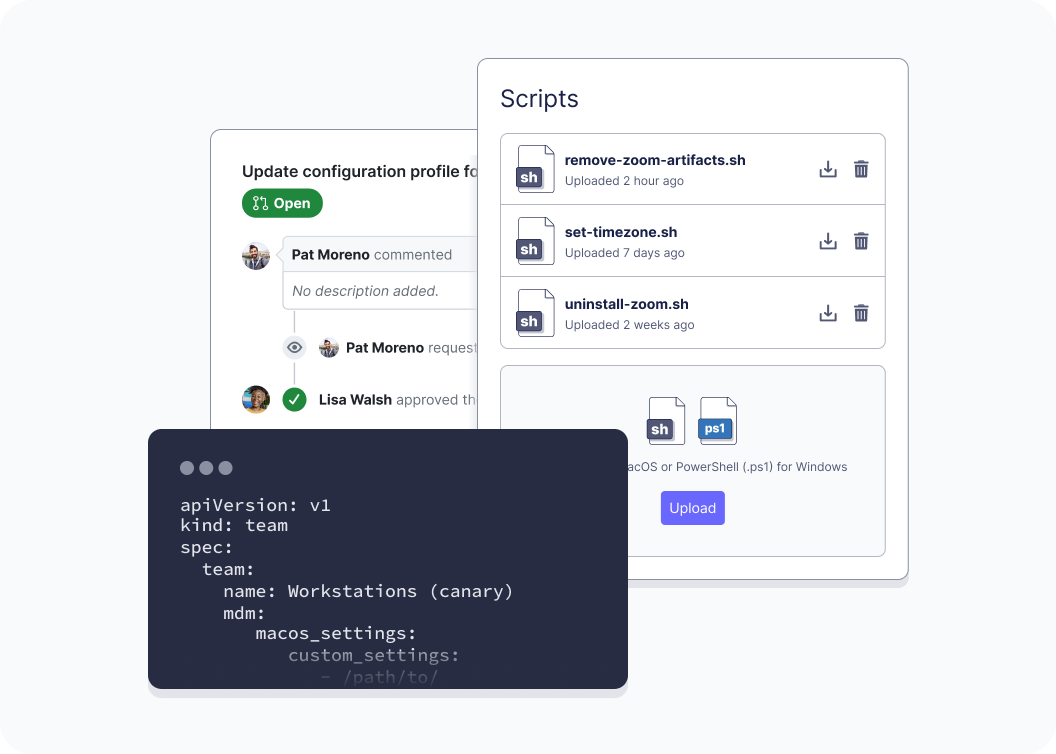
Orchestrate anything
Remote-control IT tasks on every kind of computer – even you, Linux.
Write and run scripts remotely, report progress, and replay queued up tasks on computers that went offline.
Optionally integrate Google Calendar to make changes when certain users’ devices are actually free.
Deep context from your environment
Get device context down to the chip level on every endpoint to help you make the right decisions.
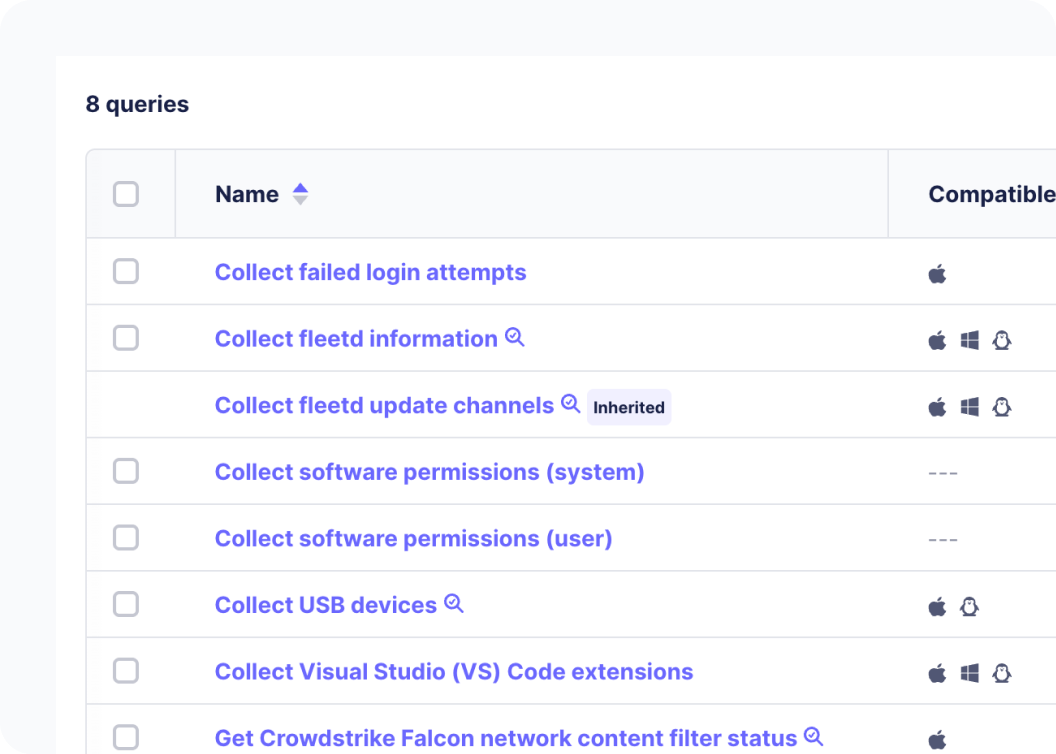
Gather real-time data by executing lightweight queries across all devices.
Access over 300 tables of system state data. Use presets or create your own queries.
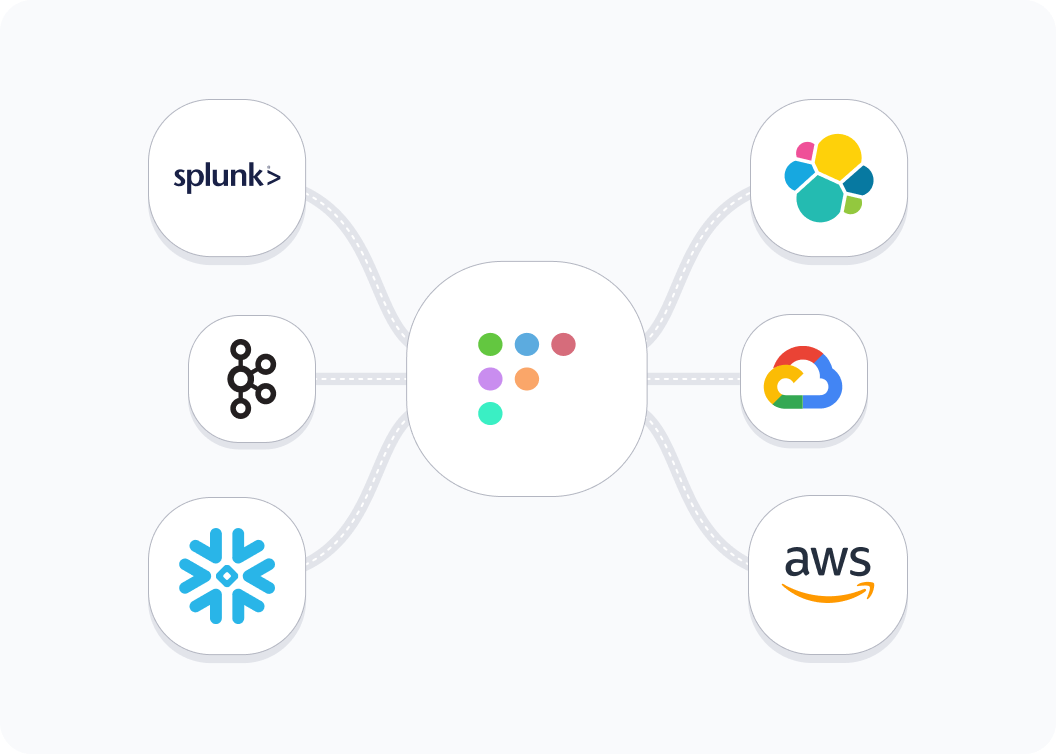
Data portability
Ship data to any platform like Splunk, Snowflake, or any streaming infrastructure like AWS Kinesis and Apache Kafka.
Extract data and correlate it with your log aggregator, SIEM, or data lake.
Ease your logging burden, pull the data you need.
“Zero” trust, fewer tickets
You can use Fleet’s API to customize every aspect of conditional access – even the stuff your CISO hasn’t thought of yet.
Get in front of the IdP
Gate access with common device trust policies from industry peers, or roll out your own device health checks using system data and events.
Step-by-step instructions
Show resolution steps or use custom HTML to show employees what they need to do to restore their access without waiting on a ticket. Then give it back automatically, as soon as the problems are fixed.
Live retry
Give people a way to get back to work quickly and minimize downtime. Fleet’s live query API instantly re-checks the OS version and other device state so users don’t get locked out.
Osquery on easy mode
Accelerate deployment and get more out of osquery. You don’t need to be an osquery expert to get the answers you need from your endpoints.
Remotely disable/enable agent features, choose plugins, and keep osquery up to date.
Import community queries from other security teams at top brands like Palantir and Fastly.
Implement the Center for Internet Security (CIS) benchmarks (one click, 400+ queries, supported by Fleet). Or customize exactly the queries you need.
Monitor sensitive production environments without enabling remote scripting by building the agent in "read-only" mode.
Open security tooling
Consolidate your security tooling on top of open data standards like YAML, SQL, and JSON.
Incident response (IR)
Contain and recover from breaches using live data, remote commands, and automated workflows.
Detection and response
Ship logs and alerts when unusual behavior is detected. Run scripts on demand or when alerts trigger.
File access monitoring (FIM)
Specify files to monitor for changes or deletions, then log those events to your SIEM or data lake.
Security posture
Identify security misconfigurations and vulnerabilities and prioritize risks that matter to your organization.
Threat management
Use attack signatures from threat intelligence sources to scan and resolve indicators of compromise (IOC).
Osquery made easy
Collect exactly the data you need from your production infrastructure across every cloud and data center*.
*Companies like Fastly and Gusto use Fleet in production with hundreds of thousands of endpoints, including containers, OT, and laptops.







